User Tools
Sidebar
Add this page to your book
Remove this page from your book
Table of Contents
2.3.4.2 State of Data Taxonomy
Overview
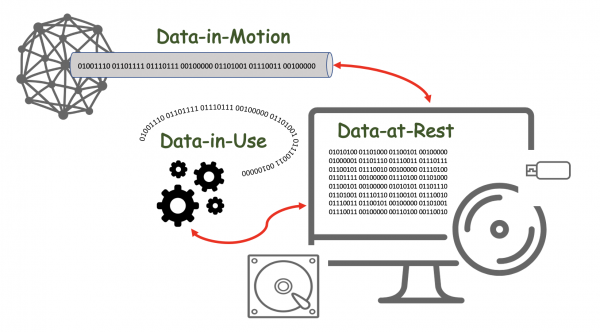
Data can exist in many states depending on how it is being used. The risks and concerns about Data in each of the different states are also important. Often, the primary focus for understanding data is to concentrate on Data-at-Rest. Although this data is relatively static, it can change over time. In the past, there was little concern for Data-in-Motion, which can have serious effects on Reliability, Maintainability, and Availability (RAM), as well as, Securability and can leave a system vulnerable to breaches. With the advent of HTTPS, these vulnerabilities are mitigated. The latest issue has become the need to secure Data-in-Use. A recent WhatsApp data breach 1) found that switching data between image filters could cause memory corruption followed by a crash that left data exposed.
Figure 1 graphically represents the different Data States within a system. Most systems are now able to handle the Data-in-Motion and the Data-at-Rest issues but have traditionally relied on physical security to protect Data-in-Use.
Data States
The only way to control access to the data at the various Data States is to control all aspects of the system:
- Data Storage
- Data Transmission
- Data Processing
Therefore, a very important Function Decision to make is what is the nature of the Distributed System Network Access Control.
Network access control taxonomy classifies the types of access individuals (i.e., nodes) have from outside and from within the node network. The two main classes of access control are permissionless and permissioned.2)
Within each of these two classifications it is possible to have public and private access. Public and private access define who is able to write data onto a network or ledger. In contrast, open (i.e., permissionless) and closed (i.e., permissioned) determine who is able to read the data. Networks are classified as3):
- public and open
- public and closed
- private and open
- private and closed
Data can exist in the following states:
[char][✓ char, 2022-03-17]New section - review plus all subsections